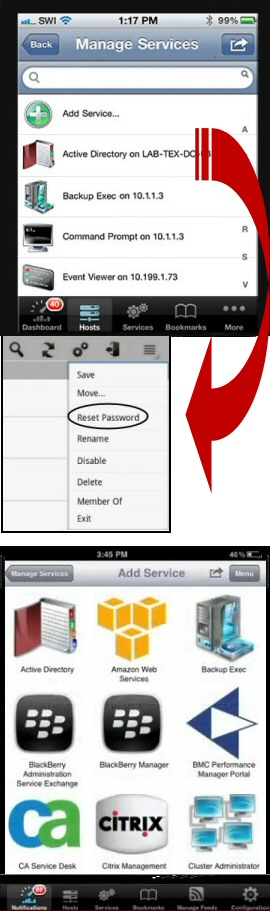
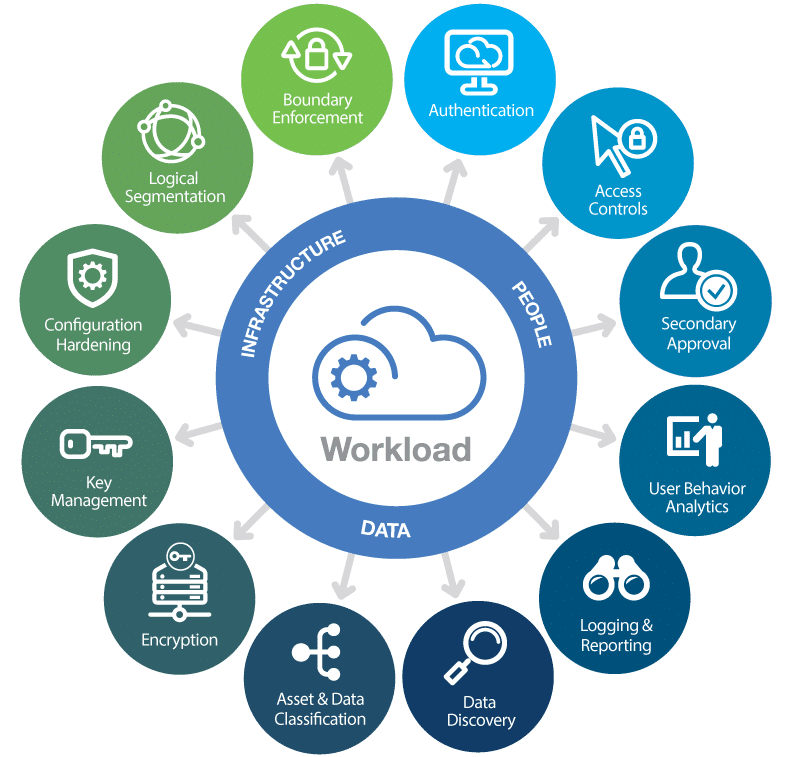
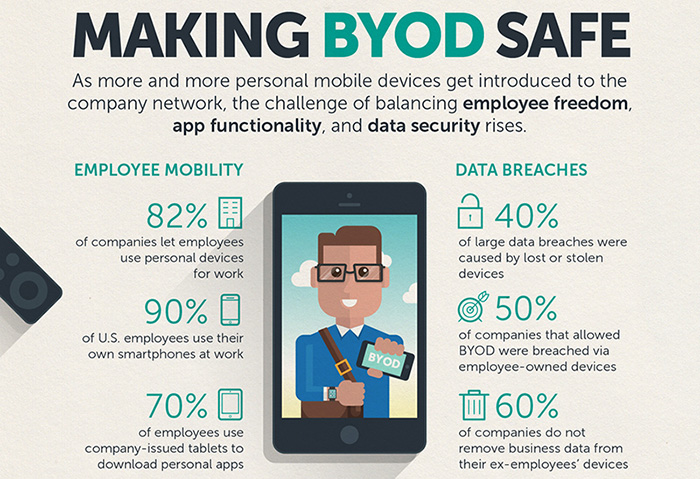
Datacenter Density: The Future of IT Infrastructure
Datacenter density is rapidly becoming a critical consideration for businesses as they strategize their IT infrastructure in the post-PC era.As organizations increasingly adopt cloud expansion initiatives, the quest for optimal datacenter density ensures that they utilize resources efficiently while catering to the monumental growth in data.