Cloud security has emerged as a critical concern in today’s digital landscape, especially for businesses relying on cloud data protection. With cloud computing risks becoming more pronounced through various high-profile hacks, companies must prioritize secure cloud storage solutions to safeguard their sensitive information. As organizations weigh the importance of choosing a reliable cloud provider, understanding effective cloud security measures is paramount. The implications of data breaches can be devastating, not only leading to financial losses but also irreparable harm to a company’s reputation. Consequently, it is essential for businesses to adopt a thorough approach to ensure their data remains protected in the cloud.
When discussing the safety of digital information, the terms ‘cloud protection’ and ‘data security in cloud environments’ frequently surface, emphasizing the vigilance required to combat potential threats. As companies transition to virtual storage systems, concerns regarding cybersecurity and the implications of data breaches remain at the forefront of strategic planning. The evaluation of various cloud services can significantly impact the operational efficiency and integrity of a business’s data assets. This necessitates a comprehensive understanding of cloud safeguards, including data encryption and compliance standards, which are essential to fortifying a company’s digital defenses. Thus, exploring innovative protection measures and selecting reputable providers is vital for maintaining a secure cloud environment.
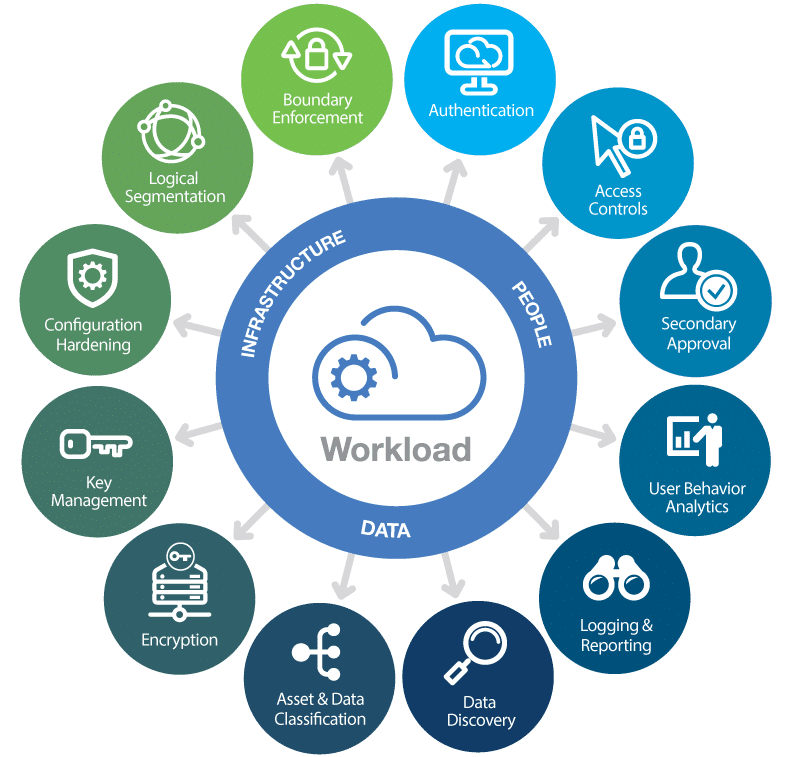
Understanding Cloud Security Measures
Cloud security measures are paramount in today’s digital landscape, especially as more businesses transition their data to cloud environments. Implementing robust security protocols can mitigate risks associated with cloud data protection. These measures include comprehensive encryption, strict access controls, and continuous monitoring of data flow. By utilizing advanced encryption techniques, businesses ensure that even if data is intercepted, it remains protected against unauthorized access. Additionally, employing strict access controls can limit who can access sensitive data, thus reducing the potential for insider threats.
Moreover, continuous monitoring plays a critical role in maintaining cloud security. This involves regularly auditing cloud systems for compliance with security standards and regulations. Businesses should also ensure that their cloud provider has a dedicated security team that is always vigilant against emerging threats. By staying proactive and addressing potential vulnerabilities before they can be exploited, businesses can strengthen their defense against data breaches and cyberattacks.
The Importance of Choosing the Right Cloud Provider
Choosing a cloud provider is not just about cost; it’s about selecting a partner that prioritizes cloud security and data protection. A reliable cloud provider will have a proven track record for security compliance and will offer comprehensive services that align with the specific needs of your business. Organizations must investigate the credentials and reputation of potential providers thoroughly — look for certifications that indicate a commitment to data security, such as ISO 27001 or SOC 2 compliance.
Furthermore, understanding where your data is stored and how it is managed is essential. Reputable cloud providers should be transparent about their data practices, including what measures they have in place for physical security, such as surveillance and controlled access to their data centers. A well-established provider will also implement a multi-layered security approach, integrating everything from firewalls to intrusion detection systems. Companies should ensure that the cloud provider conducts regular security audits to review their infrastructure, ensuring it remains resilient against threats.
Navigating Cloud Computing Risks
While the shift to cloud computing offers numerous advantages, it also introduces specific risks that businesses must navigate carefully. These risks can range from data breaches and unauthorized access to compliance issues with regulations like GDPR or HIPAA. Businesses need to conduct thorough risk assessments and consider implementing cloud data protection policies that encompass data encryption, user access tracking, and regular audits.
Additionally, understanding the shared responsibility model of cloud security is crucial. In this model, cloud service providers are responsible for securing the infrastructure, but businesses must implement their security measures to protect their data and applications. This includes ensuring that all sensitive data is properly encrypted and that access controls are in place to prevent unauthorized use. By being proactive in identifying potential risks and implementing effective solutions, businesses can harness the benefits of cloud computing while minimizing exposure to threats.
Advantages of Secure Cloud Storage Solutions
Secure cloud storage solutions provide businesses with the peace of mind that their data is protected and accessible. One of the primary advantages is the ability to scale storage resources as needed, allowing businesses to adapt to changing demands without compromising security. Secure cloud storage solutions utilize advanced technologies such as end-to-end encryption and robust authentication protocols to safeguard sensitive information.
Moreover, secure cloud storage enhances data availability and disaster recovery. In the event of a hardware failure or natural disaster, cloud storage ensures that important files can be restored quickly without significant downtime. This reliability is crucial for businesses that rely on constant access to data for operations. Additionally, many cloud storage providers offer automatic backups and replication across multiple locations, further enhancing data security and ensuring business continuity.
Best Practices for Cloud Data Protection
Implementing best practices for cloud data protection is essential for minimizing risks associated with cloud storage. These practices include employing data encryption both at rest and in transit, utilizing strong access controls, and conducting regular security audits. Encryption serves as a critical line of defense against unauthorized access, ensuring that data remains secure even if it is intercepted during transmission.
In addition to these technical measures, businesses should also invest in employee training programs to raise awareness about the importance of data security. Employees must understand common security threats, such as phishing attacks, and how to identify them. By fostering a culture of security awareness, companies can further protect their cloud data and mitigate the impact of human error, which is often a significant factor in data breaches.
Evaluating Cloud Providers: Key Questions to Ask
Before selecting a cloud provider, it’s crucial to ask specific questions that can uncover their security measures and reliability. Inquire about their data security practices, including how they handle data encryption, backup procedures, and compliance with industry standards. Understanding whether they provide multi-factor authentication and if they conduct regular security assessments can provide insight into their commitment to security.
Another important aspect to consider is the provider’s incident response plan. Ask how they would handle a data breach and what measures are in place to notify clients in the event of a security incident. A transparent response strategy indicates a mature and responsible cloud provider that prioritizes customer safety and data integrity, providing reassurance to businesses looking to safeguard their critical information.
Cloud Security Myths Debunked
Many misconceptions exist surrounding cloud security that can lead businesses to hesitate when transitioning to cloud services. One common myth is that public cloud storage is inherently less secure than private cloud solutions. The truth is that many public cloud providers invest heavily in advanced security measures that small to medium-sized businesses may not afford independently. These providers are often at the forefront of the latest security technologies and practices, making them highly secure environments for data.
Another prevalent myth is that moving to the cloud automatically means losing control over data. In reality, opting for a reputable cloud provider allows businesses to maintain control over how their data is stored and accessed. Organizations can implement their security measures while leveraging the infrastructure and expertise of the cloud provider to enhance overall data protection and compliance.
The Future of Cloud Security: Trends and Innovations
The future of cloud security is continuously evolving, with innovations aimed at addressing the increasing sophistication of cyber threats. One significant trend is the growing adoption of artificial intelligence and machine learning in security protocols. These technologies can help identify abnormal behavior, detect potential threats in real time, and automate responses to security incidents, allowing businesses to stay one step ahead of cybercriminals.
Additionally, the rise of zero-trust security models is gaining traction in cloud environments. This approach assumes that threats could originate both inside and outside the organization, prompting businesses to verify every request and access attempt continuously. Implementing a zero-trust model can significantly enhance the security posture of organizations utilizing cloud services, ensuring that data remains secure against unauthorized access and breaches.
Frequently Asked Questions
What are the key cloud security measures to consider when choosing a cloud provider?
When selecting a cloud provider, prioritize cloud security measures such as robust physical security (including 24/7 monitoring and biometric access), up-to-date software patches, comprehensive firewalls specific to cloud environments, and strong data encryption for storage and transfers. Ensuring that the provider can offer fast data recovery options and has solid backup practices is also crucial for maintaining cloud data protection.
How can businesses ensure cloud data protection against potential security risks?
To ensure effective cloud data protection, businesses should conduct thorough assessments of potential providers, focusing on their security infrastructure, compliance with data protection standards, and their capabilities in applying multi-layered security measures. Implementing additional layers of security, such as encryption and access controls, further mitigates cloud computing risks.
What are common cloud computing risks that companies should be aware of?
Common cloud computing risks include data breaches, inadequate access controls, loss of data control, and compliance violations. Additionally, risks associated with the multi-tenant architecture, such as unauthorized access due to poor partitioning of resources, can compromise cloud data protection.
How does secure cloud storage differ from traditional data storage solutions?
Secure cloud storage typically offers more advanced encryption protocols, redundancy, and automatic updates compared to traditional data storage. Cloud providers invest heavily in security measures and infrastructure, making them less attractive targets for hackers, while also providing scalable resources that can adapt to a business’s changing needs.
What should companies ask potential cloud providers to assess their security capabilities?
Companies should inquire about a cloud provider’s physical security measures, data backup practices, compliance with industry standards, capabilities for encryption and secure data transfer, and the availability of specialized solutions for sensitive data management. These questions are essential to evaluate the effectiveness of the provider’s cloud security measures.
Why is choosing the right cloud provider critical for business security?
Choosing the right cloud provider is critical because the security of your data relies on their infrastructure and practices. A provider with poor security measures can expose your sensitive information to breaches and loss. Thus, investing in a reputable provider with proven security capabilities is paramount for effective cloud data protection.
What role does encryption play in cloud security?
Encryption is a vital component of cloud security, protecting data during transfer and at rest. It ensures that unauthorized users cannot access sensitive information, thereby enhancing cloud data protection. Businesses should ensure their cloud provider employs strong encryption standards and offers encryption options for customer data.
How can businesses mitigate risks associated with shared cloud environments?
To mitigate risks in shared cloud environments, businesses should ensure their cloud provider implements strong isolation measures that compartmentalize data access. Additionally, businesses should leverage strong authentication methods and monitor user access and actions within the cloud environment to enhance overall cloud security.
What are the implications of poor cloud security for businesses?
Poor cloud security can lead to severe implications for businesses, including data breaches, financial losses, reputational damage, and legal repercussions stemming from non-compliance with data protection regulations. It’s imperative for businesses to prioritize cloud security in order to protect their data effectively.
How do compliance standards impact cloud security measures?
Compliance standards, such as PCI DSS and GDPR, set the benchmark for cloud security measures that businesses must adhere to in order to protect sensitive data. Cloud providers that comply with these standards are more likely to implement robust security protocols, making them a safer choice for businesses looking to enhance their cloud data protection.
| Key Points | Details |
|---|---|
| Cloud Security Concerns | Business data safety is questioned due to rising hacking incidents. |
| Impact of Data Loss | Data loss can lead to significant monetary and reputational damage to businesses. |
| Local vs Cloud Storage | Reverting to local backups may increase overall risk and recovery time. |
| Cloud Providers Security | Cloud providers invest more in security and physical safety than individual businesses can. |
| Choosing the Right Provider | Select providers with proven track records and strong security measures. |
| Verification Questions | Ask essential questions before selecting a cloud provider to ensure adequate security. |
Summary
Cloud Security is a critical factor for businesses as the frequency of security breaches continues to rise. It is imperative for firms to carefully evaluate cloud storage solutions, not only to protect their data from cyber threats but also to ensure compliance with regulatory standards. Investing the time and resources to select a competent cloud provider, equipped with strong security measures and a solid reputation, can safeguard valuable data and enhance overall security strategy. Businesses must not overlook the importance of cloud security to maintain their integrity and operational continuity.